Websockets? was a challenge in the web category for UTCTF 2022, in the end it has {{ page.solves }} Solves and it was worth {{ page.points }} Points. It was relatively easy.
We find this website without much information or input, checking its source we find a new page /internal/login and a username admin.
Going to this we now see a login, it requires a username and password. Lets open its source and see what we can find. There is a comment it says the following
| |
So the password will be 3 diget’s long? So it will have a range from 000 to 999.
There also is a JavaScript file, opening it shows us something interesting. The login uses websockets to verify the password, we can easily bruteforce it. Lets write a small script using python.
| |
^ A download for this script can be found here
This code uses multithreading to get the correct pincode as quickly as possible. It also makes sure that the pincode is padded with zero’s in front. Running this results in the following output.
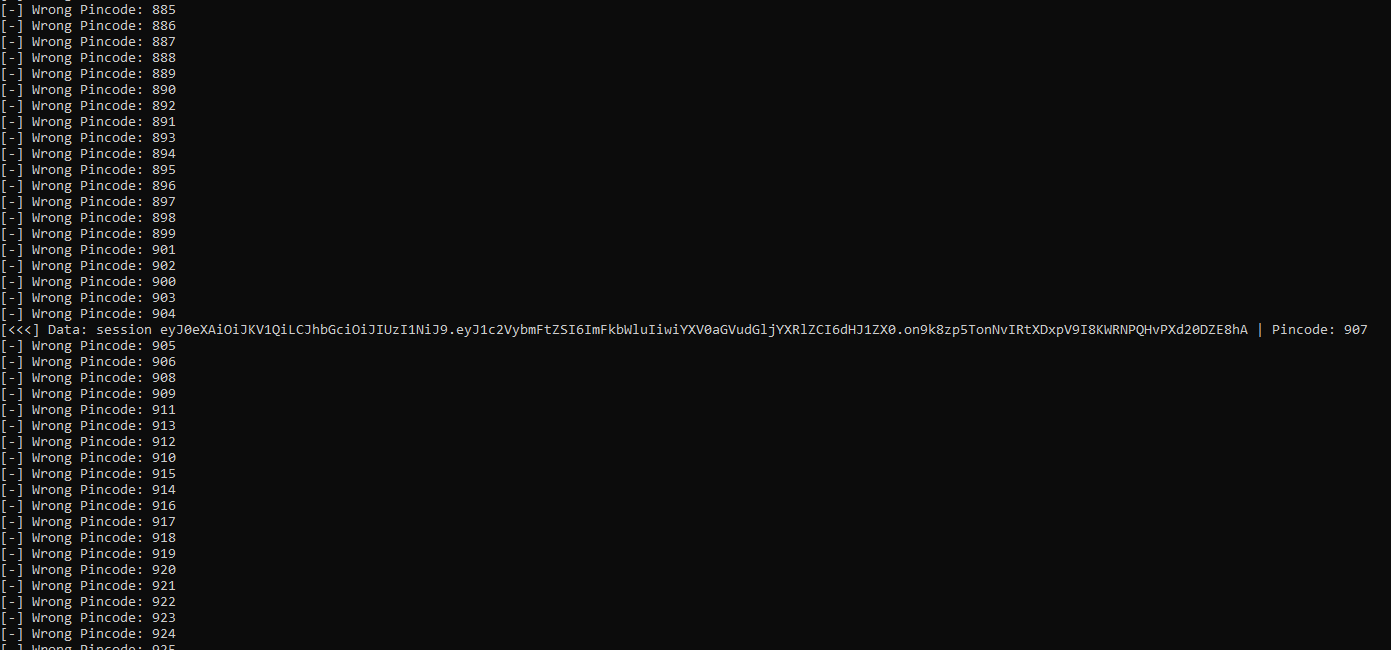
The pincode it found is 907.
Lets login with this acquired pincode, and we got the flag! utflag{w3bsock3ts}