Ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8065/tcp open unknown
Reconnaissance
On port 8065 there is a Mattermost Server, its a sort of slack but selfhosted.
Mattermost is an open-source, self-hostable online chat service with file sharing, search, and integrations. It is designed as an internal chat for organisations and companies, and mostly markets itself as an open-source alternative to Slack and Microsoft Teams.
In the next image, we can see that an email is needed for mattermost.

We cant use our own email but we need an @delivery.htbmail address.
How can we get an @delivery.htbmail address, lets check out what’s on port 80 maybe we find something useful there.
On port 80 there is a a vhost for helpdesk.delivery.htb which has helpdesk software based on OSTicket.

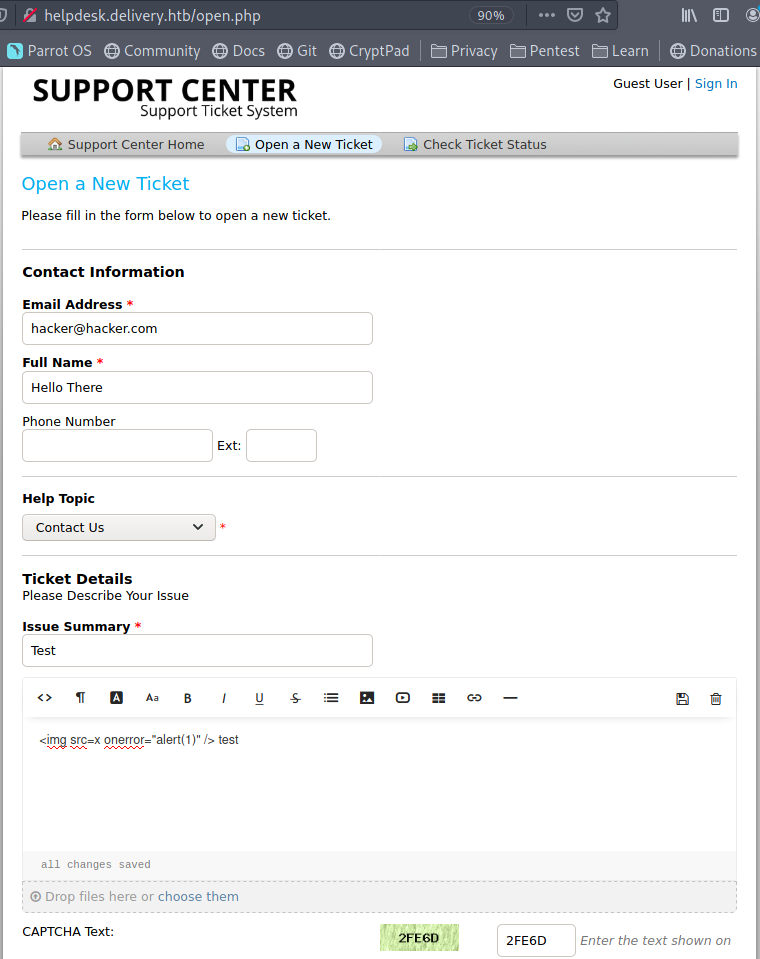
When we try to make a ticket we can see it asks for some information, lets enter a random email address in there and check if it accepts it. Make sure to remember what you entered.
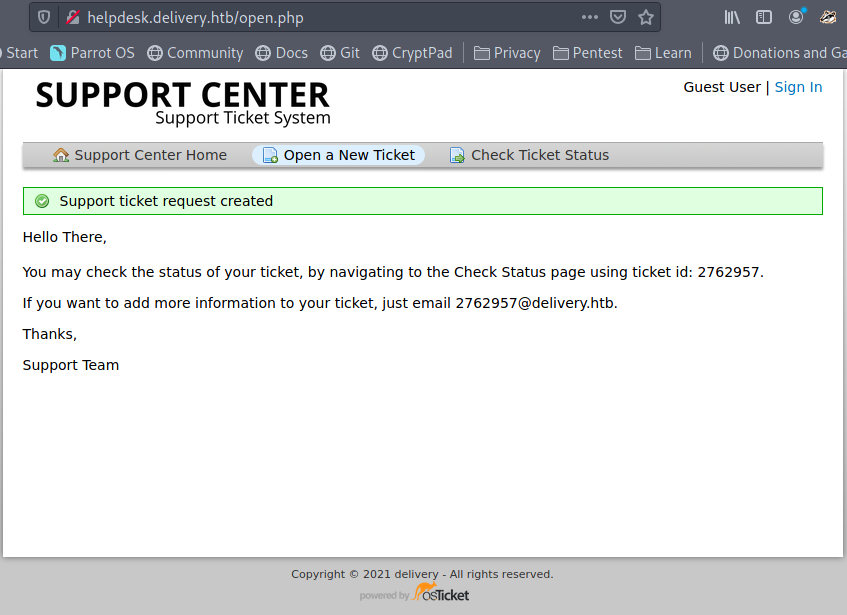
It worked, on the page we now see a ticket id and an email. Awesome we get an @delivery.htb mail address, also what gets send to it will be displayed in the ticket.

Now make an account using the email address you got when making a ticket on mattermost.
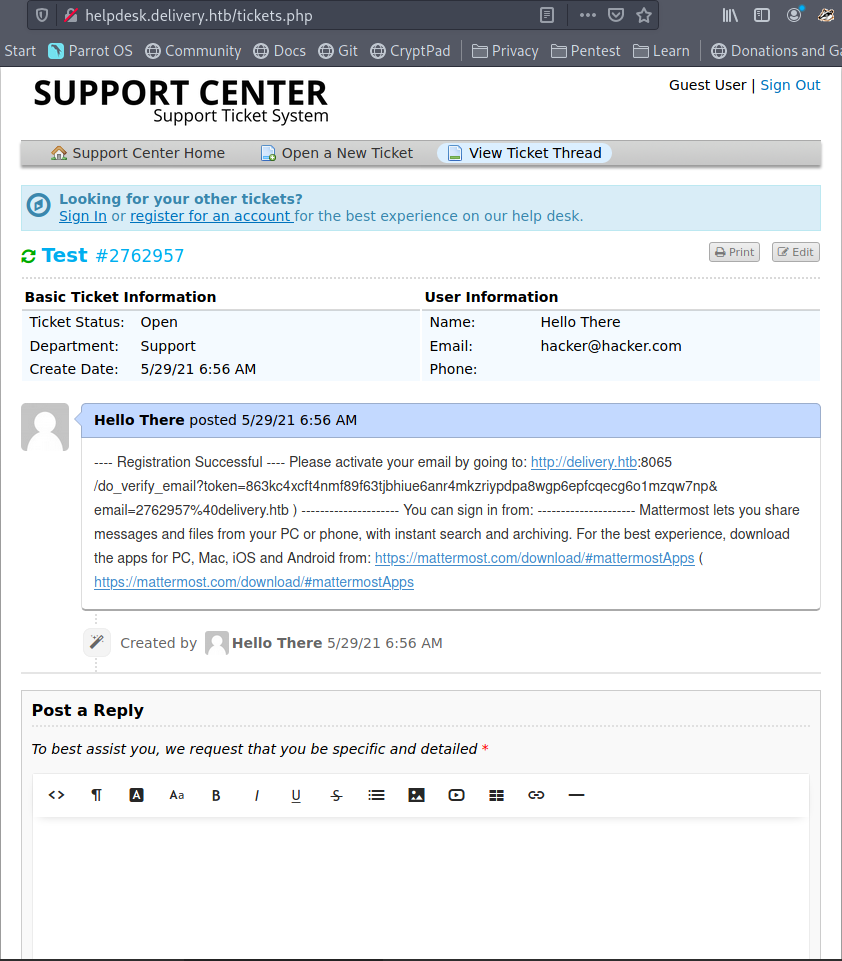
After this refresh the helpdesk page for the ticket and you should see something like this, a confirmation URL for the account. After opening the URL (make sure to use the full one), you will be redirected to the login page.
Login using the password you chose. We are in it asked for the teams we want to join, lets click on Internal.And we are in and can read the chat.

Gaining Shell
At the top of the chat we see a message that says
| |
It gives us credentials for SSH, Username: maildeliverer and Password: Youve_G0t_Mail!.
After logging in, we can get the flag!
| |
Enumeration
In the home directory there is a .mysql_history file, this tells us there is a MySQL server running. The MySQL server may also contain password hashes.
Now lets see if we can find the credentials for it. Maybe inside the mattermost configuration file, it can be found in /opt/mattermost/config/config.json
| |
Yup it is in the configuration file, Username: mmuser and Password: Crack_The_MM_Admin_PW.
Privilege Escalation
Lets connect to MySQL and see what we can find.
| |
So now that we are in MySQL, lets check what tables we have.
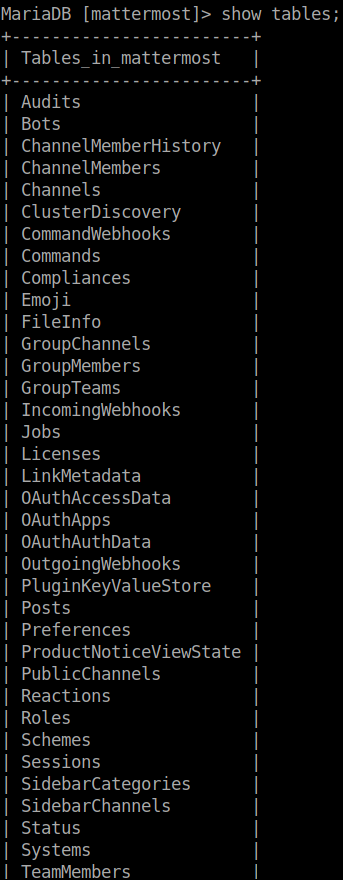
The table Users looks interesting, this may contain the passwords.

Lets run the following query to see what’s in the table
| |
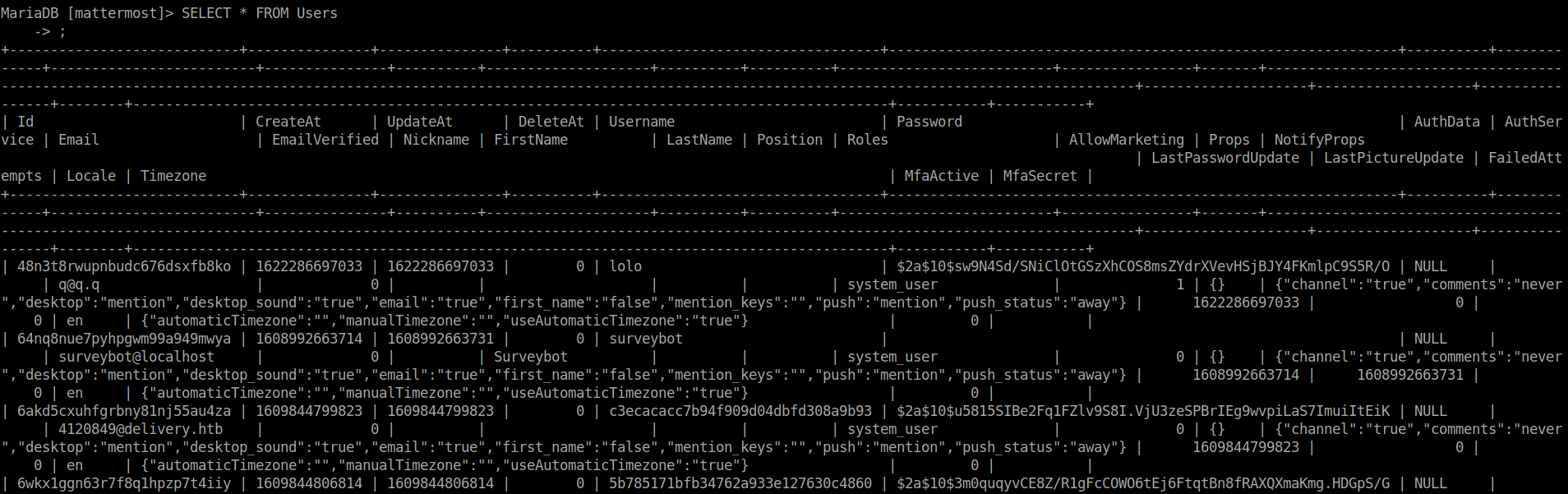 Looks like it has a username and password field. Lets select those, where the username is ROOT
Looks like it has a username and password field. Lets select those, where the username is ROOT
| |

And we find the password hash for the root user.
username: root and password: $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO
Lets start cracking that hash. We can find in the chat that the password is a variant of PleaseSubscribe!.
Also please create a program to help us stop re-using the same passwords everywhere…. Especially those that are a variant of “PleaseSubscribe!” PleaseSubscribe! may not be in RockYou but if any hacker manages to get our hashes, they can use hashcat rules to easily crack all variations of common words or phrases.
Put the hash into a file root.hash and put PleaseSubscribe! into a file root.dict.
And use the following command.
| |
What does this command do?
- It sets the hash type to 3200, this is bcrypt.
- It sets the attack mode to 0, this is straight and will only use the wordlist and apply the rule file.
- It sets the workload profile to 1, this is the lowest one and perfect for my VM.
- It uses hash from the
root.hashfile. - It uses the password from the
root.dictfile. - It uses the
/usr/share/hashcat/rules/best64.rulefile for the password rules.
After a few minutes this will return with a password and it is PleaseSubscribe!21.
Lets switch to the root user.
| |
